- What is BitLocker?
- Who should be using Bitlocker?
- How can I obtain it?
- How do I use BitLocker to encrypt my laptop?
- Where can I find written documentation?
- What should I know about decryption?
- What restrictions are there when traveling out of the country with an encrypted laptop?
- Resources
Q. What is BitLocker?
A. BitLocker Drive Encryption is an integral security feature for Windows computers. It provides protection for your computer's operating system as well as the data stored it, ensuring that the data remains encrypted even if the computer is tampered with when the operating system is not running. This helps protect against "offline attacks," those made by disabling or circumventing the installed operating system, or made by physically removing the hard drive to attack the data separately.
Q. Who should be using Bitlocker?
A. ISG recommends that faculty and staff enable BitLocker if they use laptops containing data with a risk of Level 2 or 3 (especially frequent travelers).
Q. How can I obtain it?
A. BitLocker is built into the Windows operating system, but is not enabled by default. Your IT Support Professional will determine if you need BitLocker enabled and perform the necessary steps.
Q. How do I use BitLocker to encrypt my laptop?
A. Your IT Support Professional will enable BitLocker.
Q. Where can I find written documentation?
A. Microsoft provides an overview and guide for using BitLocker with Windows 7, 8.1, 10 and 10 Mobile.
Q. What should I know about decryption?
A. In the event that you feel your computer needs to be decrypted contact your IT Support Professional, or if none, the IT Service Center. Note that the decryption process will take about the same length of time as encryption did.
Q. I have a computer encrypted but when I start it up, I get a Bitlocker screen about:
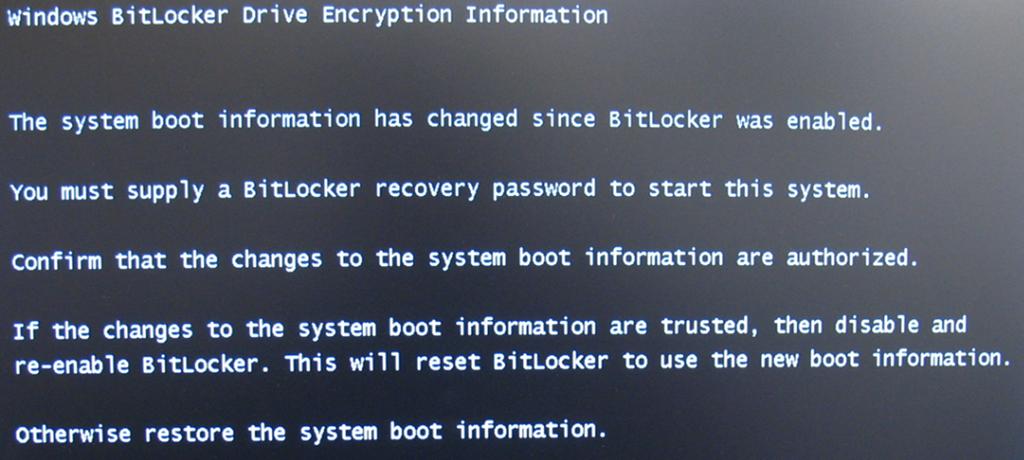
A. Bitlocker has detected that something with your computer hardware has changed. This is a security feature designed to protect your data. For example, someone could have stolen your computer and is attempting to bypass the normal startup sequence. Follow the step below to obtain a recovery password. Please note, you will need access to another device with a web browser.
- Press any key to continue, the next screen will be similar to this:
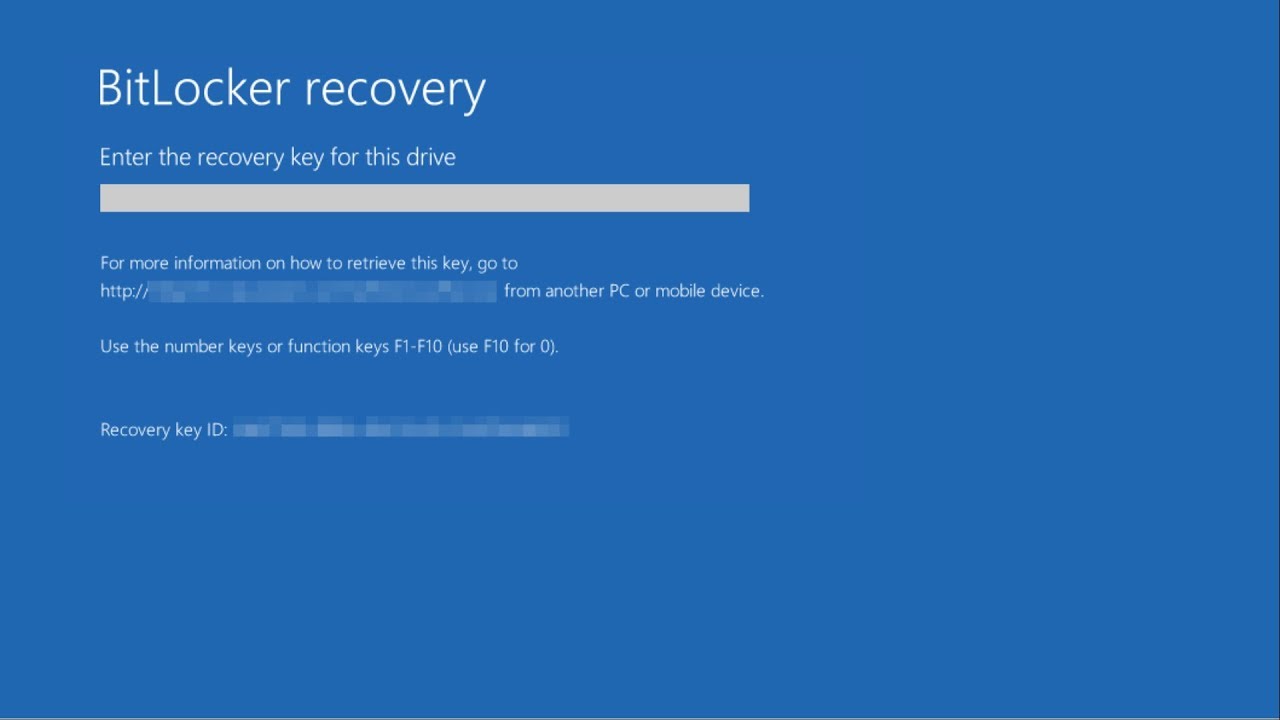
- Go to the Self Service Recovery site: https://bitlocker.brown.edu.
- When prompted, enter your Brown UserID and Password.
- Check the box next to "I have read and understand the above notice".
- At this screen, enter the first 8 digits of "Recovery Key ID" from the screen above from your computer:
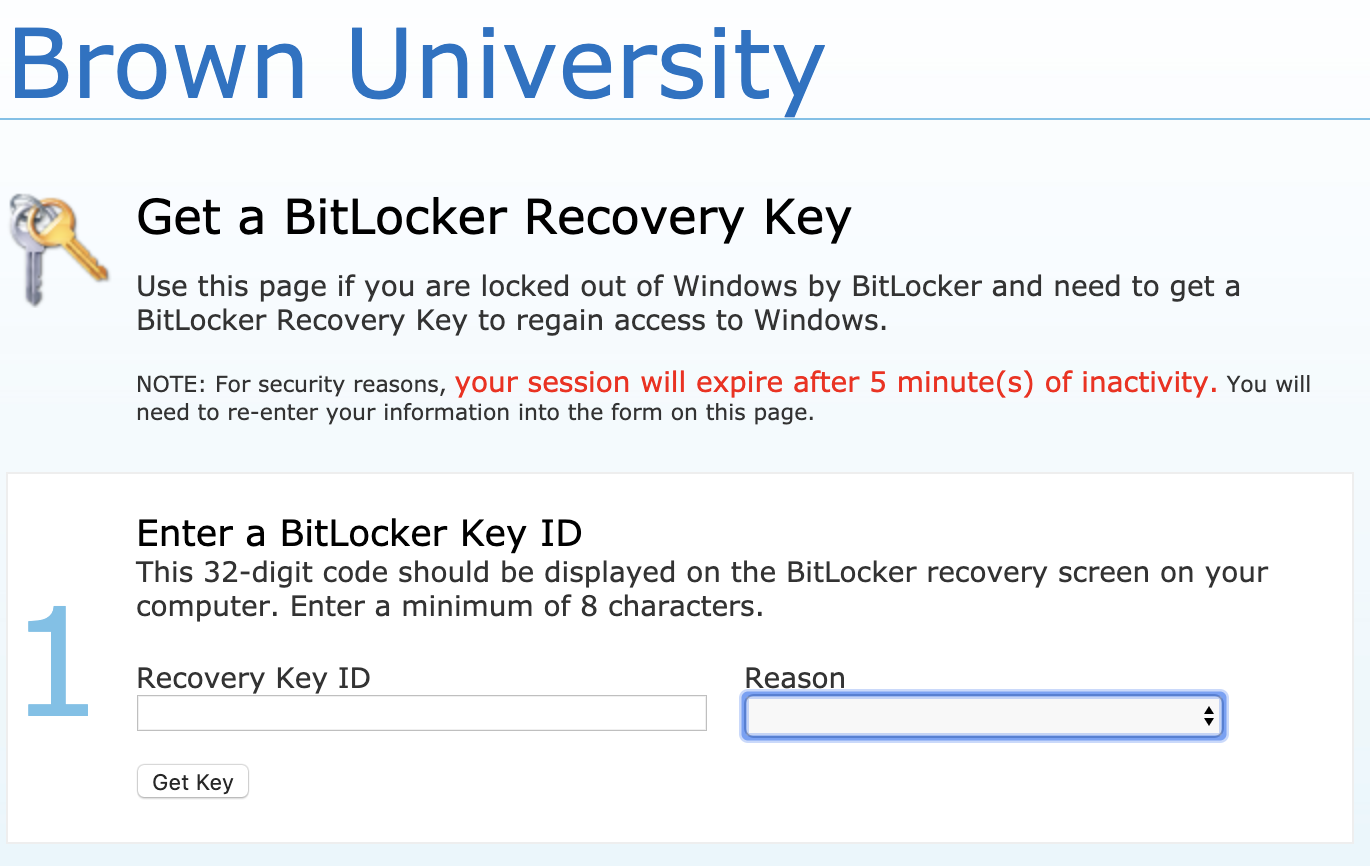
- Finally, enter the 48-digit code into the recovery screen on your computer.
Q. What restrictions are there when traveling out of the country with an encrypted laptop?
A. U.S. federal regulations control the export of "encryption commodities, software and technology" (see Code of Federal Regulations, Title 15, Section 740.17). There are, however, license exceptions that allow taking encrypted laptops, provided that the traveler returns within the year and "retains effective control and ownership." This coverage is global except for a handful embargoed and sanctioned countries designated by the U.S. government. Travel to any of these countries requires that you remove any encryption technology from your laptop before entering it.
In addition, since laws can change at any time and some countries ban or severely regulate the use of encryption, you should consult country-specific information before traveling with an encrypted laptop to verify that your information is still current. In addition, any faculty, post-docs, graduate students and PI's should check-in with OVPR, read its International Travel page as well as that of the Office of Insurance and Purchasing Services , and contact the Chief Information Security Officer before travelling overseas.
Finally, note that many nations do not recognize a "personal use exemption." Before traveling to these countries with an encrypted laptop, you will need to apply to their specified governmental agency for an import license. Additional information about international encryption controls can be found at the following websites:
Resources
- Turn on Device Encryption (Windows 10)
- Help protect your files using BitLocker Drive Encryption: Windows 7 | Windows 8 | Windows 10
Internal links about traveling:
- Brown's Travel Portal and Export Controls guidelines
- International Travel Information for all Brown University Travelers
- Export Control Regulations at Brown | Brown's Export Control Policy and Procedures
Note: For questions or further information related to export controls or international research administration, please contact Juliane_Blyth@brown.edu, Senior Director, Office of Research Integrity at (401) 863-3295.
External links about traveling:
- Encryption FAQs (Bureau of Industry & Security, BIS)
- EAR Controls for Items That Use Encryption (Bureau of Industry & Security, BIS)
- Cornell University - Travel Internationally with Technology
- Department of State - Travel Alerts and Warnings
- Department of Homeland Security - "Know Before You Go" Resources
- Department of State - Websites of US Embassies Consulates, and Diplomatic Missions
- Department of State -"Smart Traveler Enrollment Program"
